Nitty-Gritty Detail Comparison of GDPR and CCPA
Detail comparison of the European Union's General Data Protection Regulation (GDPR) vs. the California Consumer Privacy Act (CCPA)
High-Level Comparison of GDPR and CCPA
A high level comparison of the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA)

CCPA Cheat Sheet
An executive summary of the California Consumer Privacy Act (CCPA) discussing scope, rights, obligations and enforcement

"Know Your Rights" under the CCPA
The California Consumer Privacy Act (CCPA) spells out 7 privacy rights for consumers
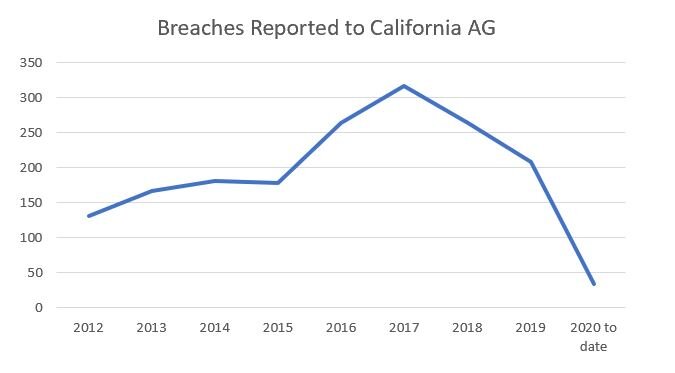
Problems with the California AG’s Reporting on Data Breaches
The California AG's reporting on data breaches turns to have a few big problems.

Drilling Down on the California Breach Notification Law
Drill down on California's Data Breach Notification Law

Looking at US Data Protection Laws in the Context of the CCPA
To understand the CCPA, you first need to understand what existing US privacy and data protection laws exist.

GDPR Cheat Sheet
A summary of the scope, rights, obligations and enforcement mechanisms found in the GDPR

GDPR's Accountability and Governance Obligations
Revisiting the GDPR's Accountability and Governance Obligations for Controllers

Back on the Horse
After taking a break after injuring my arm, ready to jump back on the blogging horse

GDPR's Key Data Processing Principles and Individual Rights
My recent blogs regarding data breaches, cybersecurity spend and the need for a comprehensive data breach notification law have consistently pointed to the European Union's General Data Protection Regulation (GDPR) as the "gold standard" for privacy and data protection.
The Need for a Comprehensive Breach Notification Law (and Then Some)
While recently drilling down into trend lines regarding data breaches and cybersecurity spend, it has became readily apparent that we are flying blind regarding the true enormity of the hacking problem we are facing.
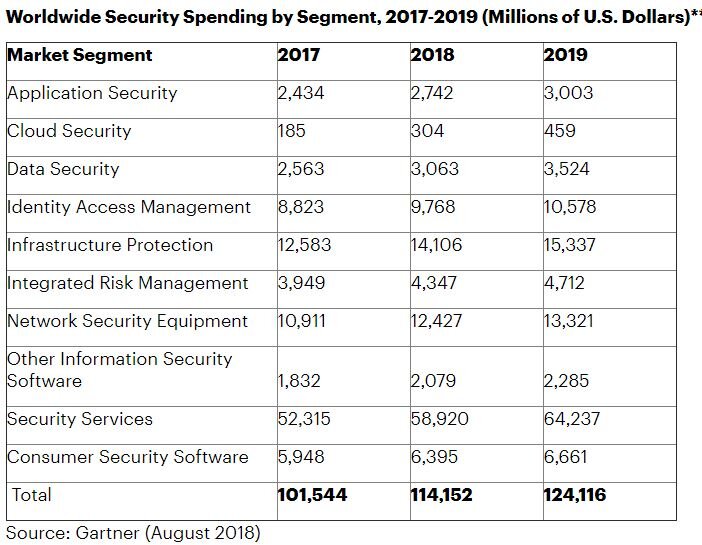
Is Security Spending Keeping Pace?
In my last two blog posts, I looked at the trend lines vis a vis data breaches from a number of annual reported breaches and compromised records, including factoring out the impact of major whale breaches. The caveat of course is this is based on what’s publicly reported.

How Badly are Data Breach "Whales" Impacting the Breach Trend Lines?
Shortly after posting “Data Breaches: So How Bad is it Getting?“, it dawned on me that it might be interesting to factor out the big “whale” breaches (e.g. Yahoo! in 2016 with 3+ billion compromised records) to get a feel for what “run rate” breach rate really is in terms of compromised records. So consider this blog post an addendum to that blog post.
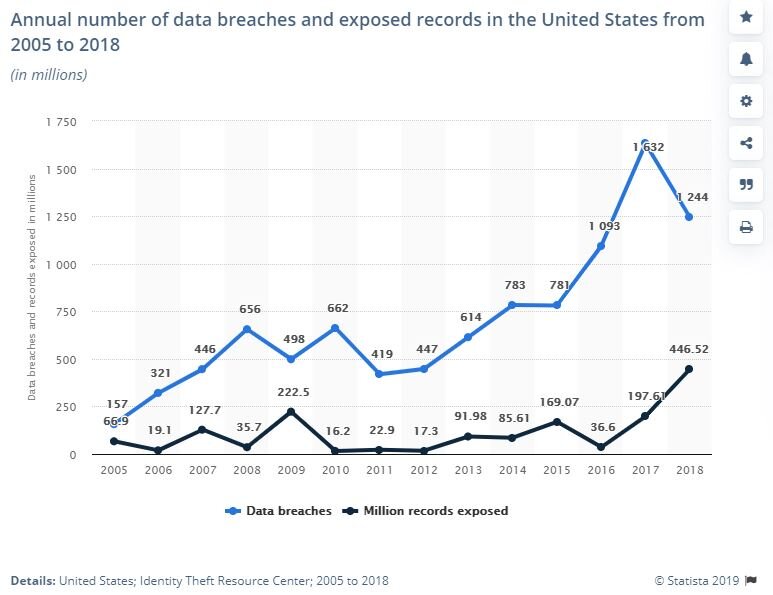
Data Breaches – So How Bad is it Getting?
The number of breaches seem to be leveling off, but the number of compromised records is growing dramatically. And it is quite evident we need a federal law for breach notification.

Jumping Back into the Cybersecurity Ocean
After living and breathing cybersecurity for 14 years, I purposely took a sabbatical in 2019 from cybersecurity (and frankly work in general). Now that 2019 is almost over, and my batteries are for the most part recharged, I have decided to pop my head up and will use the next set of blog posts to get a sense of the state of play of cybersecurity going into 2020 in terms of trends and new legislation. I will also try to sort out if there are any new approaches that have emerged to solve our cybersecurity problem.